Protecting Employees Using Secure AWS Solutions
What is TMA?
Since 2014, Deutsche Telekom AG (DTAG) has run an employee threat management system internally. Dealing with all kinds of workplace issues and threats, the ultimate aim of the system is to ensure that each employee is treated with dignity and respect and to protect the company and its employees from harm.
The threat management system follows three key steps:

Recognize: All kinds of violence have precursors. Identifying specific warning behaviours can help each employee recognize the threat of violence. Employees can report such warning behaviour to the threat management system.
Assess: The threat management system will then assess the criticality of the issue.
Defuse: The system implements countermeasures with all involved people to reduce the risk for the employee and the company.
Since data privacy and security are paramount for this project, these aspects are taken into serious consideration when architecting and implementing the solution in AWS:
All the business requirements for the TMA system mentioned above can be met using AWS. The TMA application leverages a modern containerization solution (Docker) using Amazon Elastic Container Service (ECS). This is a fully managed container orchestration service for security, reliability, and scalability.
The points below reflect the services implemented based on the security recommendations and improvements suggested by the AWS Well-Architected Review:
- Ruby on Rails as a web-application framework — introduced containerization using Docker process
- Deployments via CodePipeline managed by Elastic Container Service
- RDS PostgreSQL for data tier — multi-AZ for high availability and failover support
- GitLab (Workbench)/CodePipeline for versioning and CI/CD
- SSM Parameter Store for passwords and parameters
- Elastic Load Balancing — Application Load Balancer for availability
- AWS Key Management Service — encryption for data at rest
- AWS Certificate Manager for certificate management
- AWS CloudFormation — Infrastructure as Code
- Amazon CloudWatch — Monitoring
How T-Systems used AWS to achieve a high level of security and zero downtime deployments
Security: Due to the nature of the project, the TMA data needs to be fully protected. AWS services like Key Management Service (KMS) and AWS Certificate Manager (ACM) helped us encrypt the data at rest and data in transit. EBS volumes and RDS PostgreSQL databases are encrypted using AWS KMS keys.
Deployments: To achieve minimal disruption to business, we have adopted zero downtime deployments using AWS Elastic Container Service. In the rolling update deployment type, the service has a desired number of two tasks and a maximum value of 200 percent, i.e. the scheduler may start two new tasks before stopping the two older tasks. We made sure that the cluster resources required to do this are available. The Application Load Balancer performs health checks on the new version of the application before the old version is replaced. Using the AWS CodePipeline/Elastic Container Service, we are able to achieve Continuous Integration (CI) and Continuous Delivery (CD). This helped us in providing much faster feedback to project teams, thus adopting Agile/DevOps culture.
AWS Architecture — Security design implemented by T-Systems

AWS Architecture — CI/CD Pipeline implemented by T-Systems
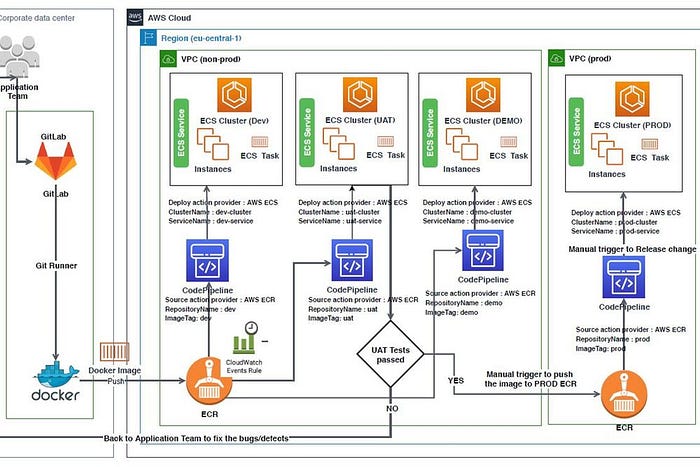
Conclusion:
Today, threat management is an integral part of Telekom’s personnel security in Germany. In fact, DTAG is the first company in Europe to employ a professional and firmly established Threat Management Assistant system.
Migrating the TMA system to AWS fulfilled all the business’s requirements, including flexibility, security, increased agility, scalability and improved business continuity. It also accelerated development of new features. Zero downtime deployments and AWS automated solutions contributed to a TMA cloud infrastructure with resulting benefits for operations.
